|
Article ID: 1781
Last updated: 03 May, 2024
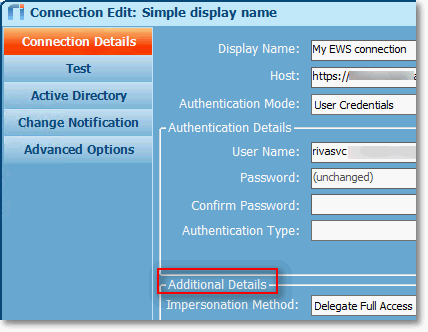
Impersonation Models in ExchangeWhen using a service account to impersonate target mailboxes connected to Riva, there are two possible Exchange Impersonation methods:
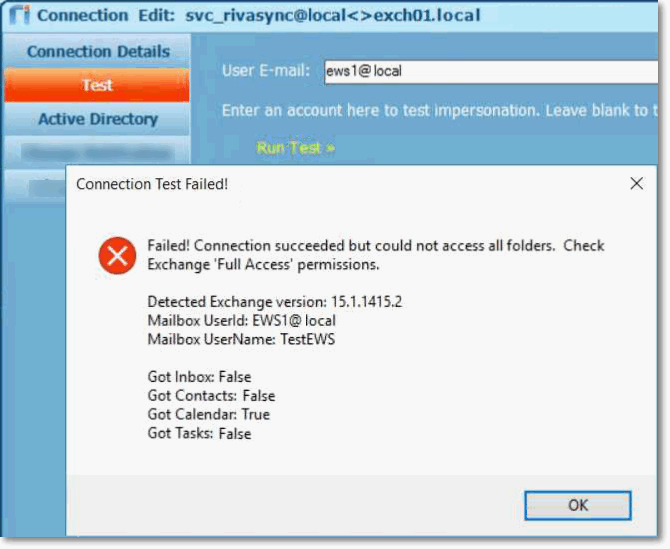
ScenarioThe ability to support both impersonation methods (access methods to a mailbox) is extremely valuable, because some organizations do not allow ApplicationImpersonation or restrict the level of access that applications can have to their users' mailboxes. In these situations, Full Access cannot be set, because the permissions scope has been narrowed to the specific folders that the Riva sync requires access to. IssueBy default, when an Exchange admin sets the mailbox permission to Delegate Access, Riva verifies the access level when connecting to EWS, and if Full Access is not configured, Riva autoswitches to ApplicationImpersonation. The problem with that autoswitch is that because the mailbox was configured with Delegate Access, the sync will always fail. The following errors messages would be displayed in the logs: SolutionIt is possible to configure Riva to sync successfully with Delegate Access. Implementation for Riva CloudImplementation for Riva On-PremiseIf limited delegate access is necessary for deployment due to privacy or security policy restrictions, the delegate permission should normally be configured in Exchange to provide access to the desired folder(s): Inbox, Calendar, Contacts, and/or Tasks. To configure Riva On-Premise to work with limited Delegate Access:
Article ID: 1781
Last updated: 03 May, 2024
Revision: 3
Views: 20
|