|
Article ID: 2310
Last updated: 24 Jan, 2023
Contents:
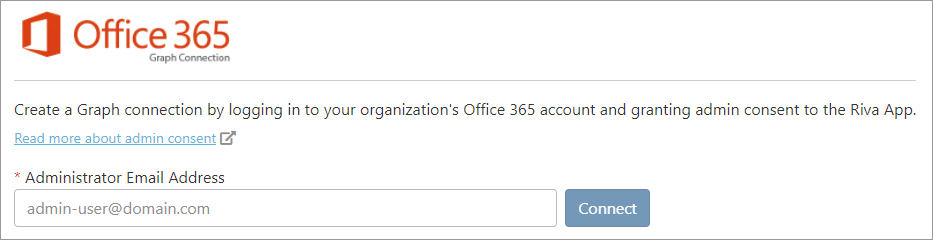
Multi-Factor Authentication (MFA)If your company requires Multi-Factor Authentication for the Riva connection account to Office 365, then you will be required to validate the account via the MFA mechanism (phone token or email address) when creating the connection. Alternatively, you could submit a request to your Exchange/Azure administrator to exclude your service account from requiring MFA. Create the Graph OAuth Connection on Riva CloudTo create the Graph OAuth connection:
How to limit specific Mailbox and User access when using "Application Permissions"When using "Application Scoped" permissions, there is a common concern that the application itself will have access to all mailboxes. There are controls specific to Exchange Online resources that do not apply to other Microsoft Graph workloads. For the specific Exchange Online scopes (including MailboxSettings.*, Mail.*, Calendar.*, Contact.*, and, Task.*), it is possible to limit the "Application Scoped" permission to specific Users and Mailbox by using the "Exchange Application Access Policy." Details on how to use the "Exchange Online Application Access Policy", https://learn.microsoft.com/en-us/graph/auth-limit-mailbox-access Refer to this Riva article for more specific details, https://kb.omni-ts.com/entry/2344/ List of Microsoft Exchange Online Application Scopes requestedBelow is a list of default Riva Cloud requested application scopes and a description of their purposes. Note: For Riva Cloud customers looking to adjust and limit scope access, please contact the Riva technical support team for guidance.
This article was:
Helpful |
Not helpful
Report an issue
Article ID: 2310
Last updated: 24 Jan, 2023
Revision: 17
Views: 0
Comments: 0
|
.png)
