|
Article ID: 1660
Last updated: 26 Apr, 2022
(Riva 2.4.45 or higher.) To create and test an OAuth Certificate-based connection to Office 365:
Step 1: Ensure That You Have Prepared Office 365Step 2: Generate a Certificate
Certificate requirementA self-signed certificate is sufficient and recommended for this type of connection, unless your organization has a policy that bans the use of such certificates. (For example, your organization might believe that using self-signed certificates may lead to complacency and using many of them may be more expensive than using signed certificates. For more information, see The hidden costs of self-signed SSL certificates.) However, if self-signed certificates are used judiciously, they are sufficient when an organization controls both ends of the connection, knows that both ends are secure, controls the connection, and knows that it is secure. For a Riva On-Premise connection to Office 365, that is the case.
Riva On-Premise and your Office 365 subscription are not strangers that need to establish trust through a certificate signed by a trusted third party: both ends of the connection are under your control and secure, and your organization can securely configure the connection; therefore, a self-signed certificate is sufficient for the connection. Generating a certificate on Windows Server 2016The Microsoft PowerShell New-SelfSignedCertificate cmdlet can be used on Windows Server 2016 to generate a self-signed certificate for the Riva connection to Office 365. Microsoft documentation mentions that the cmdlet creates a self-signed certificate "for testing purposes". The real issue is not whether a self-signed certificate could be used for testing or production; it is whether the connection and both ends of the connection are securely under your control. As demonstrated in the Certificate requirement section, a self-signed certificate for a Riva On-Premise connection with Office 365 is secure and sufficient, and in this case, Microsoft's restriction "for testing purposes" does not apply. We recommend generating, at a minimum, a 2048-bit certificate, based on the SHA256 hash algorithm. The following command is coded to do so. To generate a certificate with New-SelfSignedCertificate:
Generating a certificate on Windows Server 2012On Windows Server 2012, the Microsoft PowerShell New-SelfSignedCertificate cmdlet cannot be used to generate a self-signed certificate for the Riva OAuth connection to Office 365. Some of the required options are not available for the cmdlet on Windows Server 2012. MakeCert can be used to generate the certificate. Microsoft's webpage Certificate creation tool (Makecert.exe) mentions that MakeCert creates a self-signed certificate "for testing purposes". The real issue is not whether a self-signed certificate could be used for testing or production; it is whether the connection and both ends of the connection are securely under your control. As demonstrated in the Certificate requirement section, a self-signed certificate for a Riva On-Premise connection with Office 365 is secure and sufficient, and in this case, Microsoft's restriction "for testing purposes" does not apply.
To generate a certificate with MakeCert:
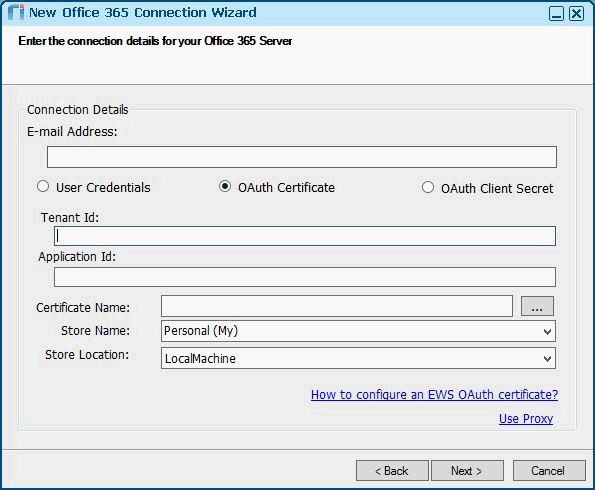
The command generates a certificate with the default validity period: from the day the certificate is generated until and including Dec. 31, 2039 11:59:59 GMT. To specify different dates, use the -b and -e extended options. For more information, see https://msdn.microsoft.com/en-us/library/bfsktky3(vs.80).aspx#Extended%20Options. Take note of the Certificate Name, Store Name, and Store Location. Those values will be used in the Riva OAuth connection to Office 365. Step 3: In Azure, Create and Configure an Application RegistrationStep 4: In Riva, Enter the OAuth Certificate-Based Connection Details
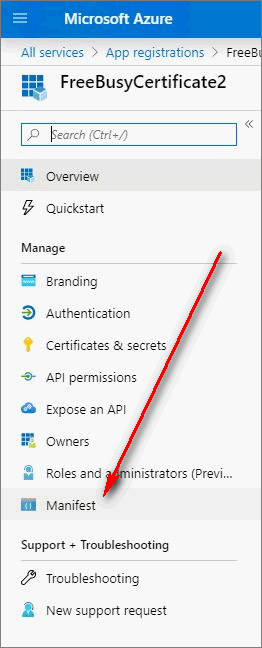
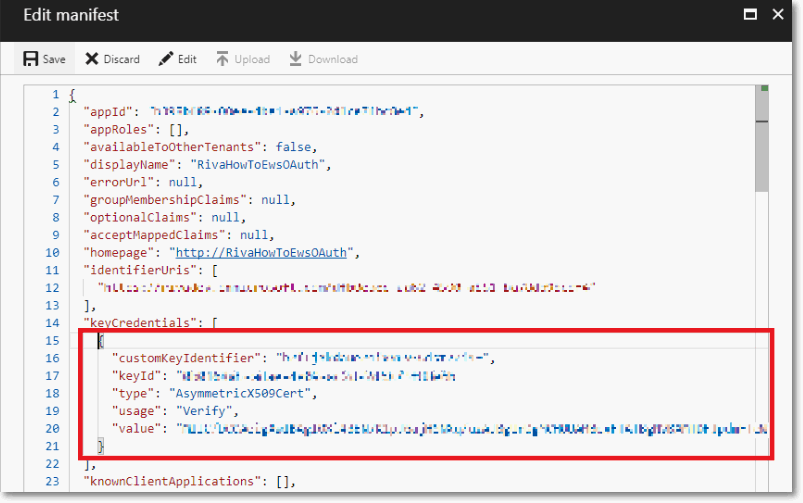
Step 5: Create the Key Identifier and Add it to the Azure OAuth Configuration
Note: The Azure Application Registration uses the X509 self-signed certificate as a secret key, which basically functions as a complex password. Step 6: In Riva, Finish Creating the Connection
Step 7: Test the ConnectionFor instructions, see Testing the Office 365 connection.
This article was:
Helpful |
Not helpful
Report an issue
Article ID: 1660
Last updated: 26 Apr, 2022
Revision: 33
Views: 6470
Comments: 0
|