Contents
- How to limit specific Mailbox and User access when using "Application Permissions"
- List of the recommended sets of permissions
- Ways to Grant admin consent
- All recommended sets of permissions are granted in Azure
- All recommended sets of permission are set up in Azure without the Admin consent
- Configuring limited permission set
How to limit specific Mailbox and User access when using "Application Permissions"
When using "Application Scoped" permissions, there is a common concern that the application itself will have access to all mailboxes.
There are controls specific to Exchange Online resources that do not apply to other Microsoft Graph workloads.
For the specific Exchange Online scopes (including MailboxSettings.Read*, Mail.Read*, Calendar.Read*, Contact.Read*, and, Task.Read*), it is possible to limit the "Application Scoped" permission to specific Users and Mailbox by using the "Exchange Application Access Policy."
Details on how to use the "Exchange Online Application Access Policy", https://learn.microsoft.com/en-us/graph/auth-limit-mailbox-access
Refer to this Riva article for more specific details, https://kb.omni-ts.com/entry/2344/
| Permission |
Permission Type |
Description |
| User.Read.All |
Application |
To lookup "email addresses" to Microsoft mailbox. |
| User.Read |
Delegated |
Sign in and read the user profile. Part of the Azure App registration process. |
| Calendar.ReadWrite |
Application |
Used to synchronize calendar items; Depending on requirements, can be limited to Calendar.Read |
| Mail.ReadWrite |
Application |
Used to synchronize email items; Depending on requirements, can be limited to Mail.Read |
| Mail.Send |
Application |
Send mail as the user. |
| MailboxSettings.ReadWrite |
Application |
Read and write mailbox settings including Categories, Time Zone and Work Hours. |
| Contacts.ReadWrite |
Application |
Used to synchronize contact items; Depending on requirements, can be limited to Contacts.Read |
| GroupMember.Read.All |
Application |
Expanding distribution lists to receive their members and for "User Gathering" process which read group memberships. |
Recommended sets of permissions are granted in Azure
(If following the complete steps from KB 2225, this section can be skipped as it's referring to this step)
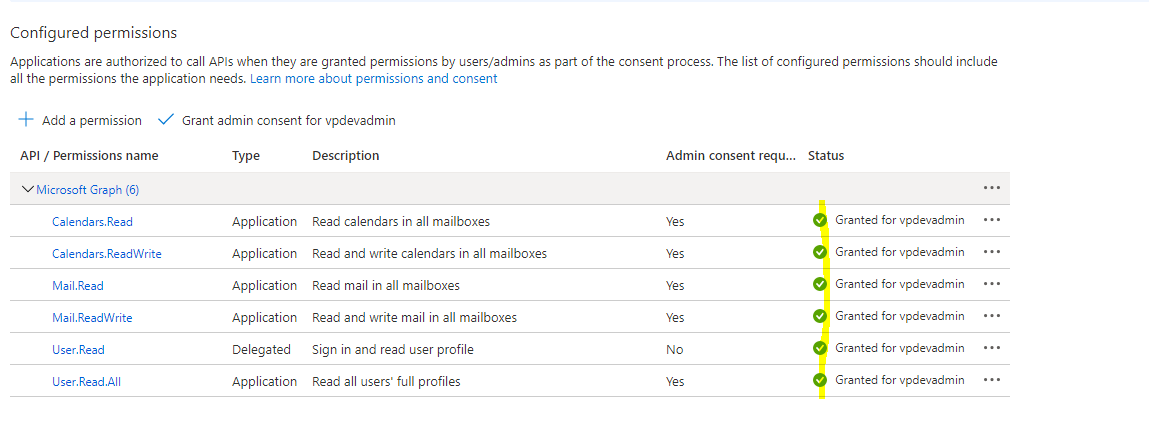
- The Admin provided all intended permissions from Azure and Grant admin consent (from Azure)
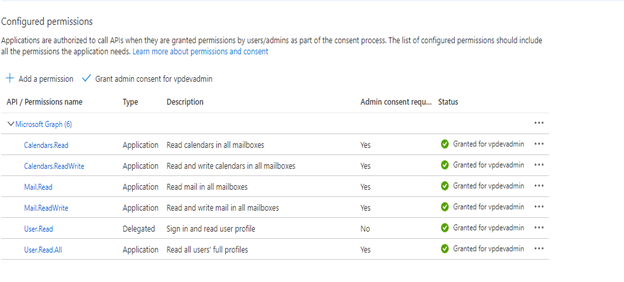
- Create a Graph connection using Riva.
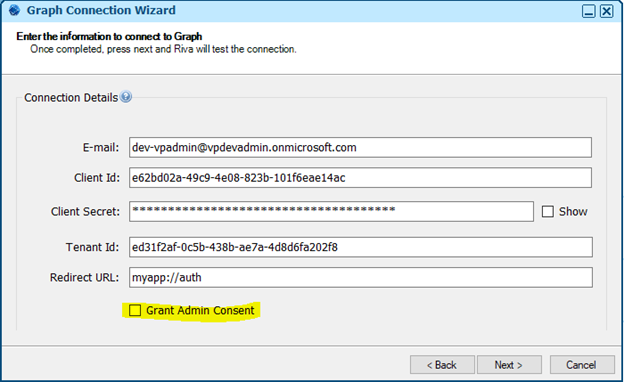
- No consent screen appears and the connection is created successfully.
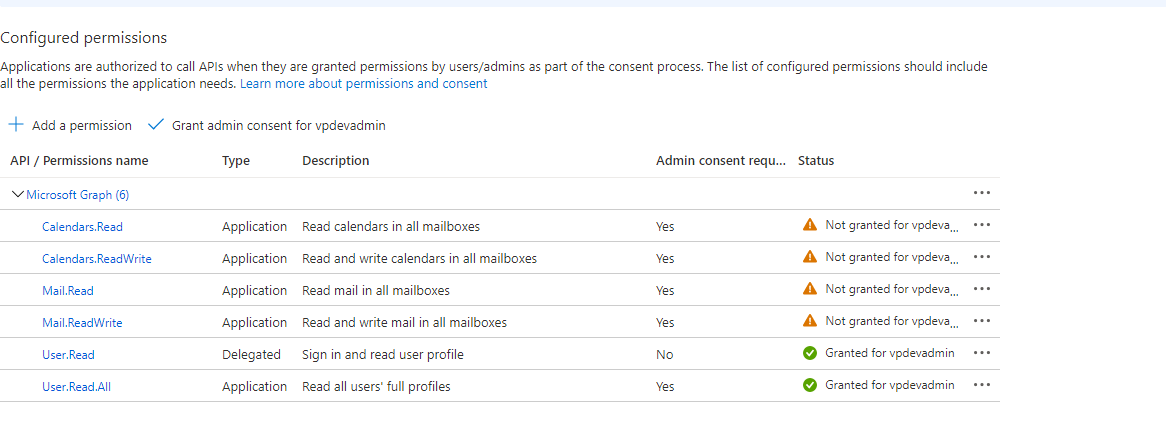
- The Admin provided all intended permissions from Azure and didn’t grant admin consent (from Azure)
- Create a Graph connection from Riva – Keep Grant Admin Consent checked
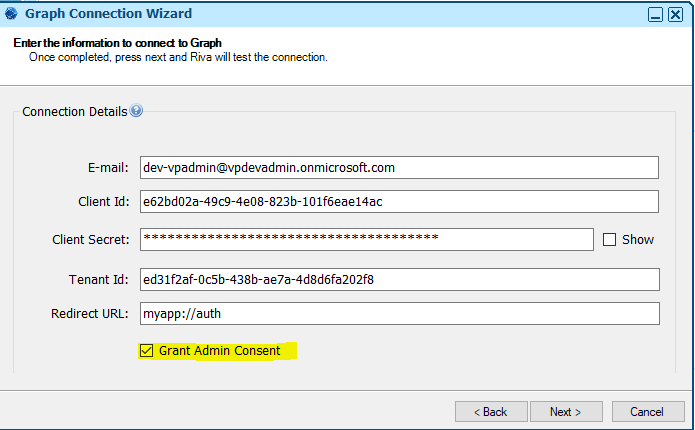
- Riva will ask to grant consent – (Admin consent will grant all the permissions - UI also does the same)
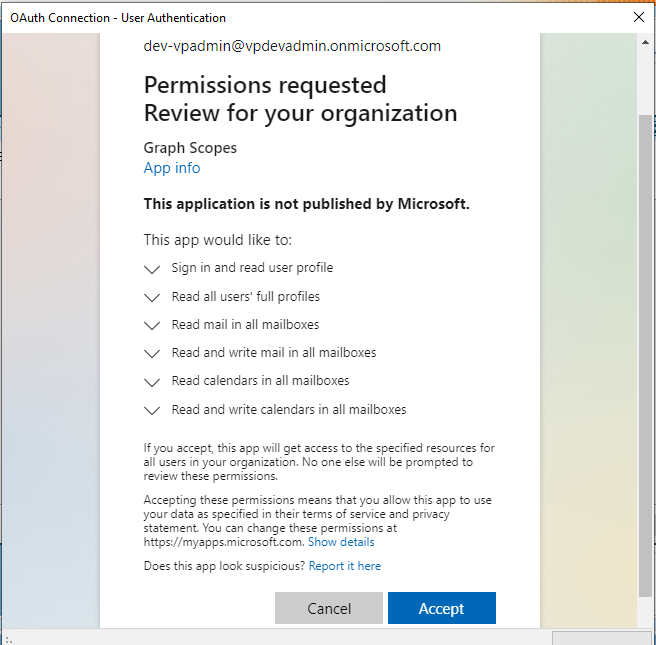
- Consent granted – Connection created successfully.
- Azure shows consent granted.
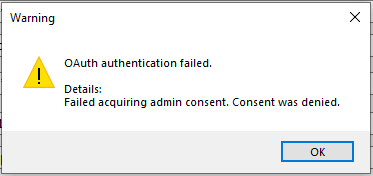
- If the consent is not granted from Riva, the following dialog will show -
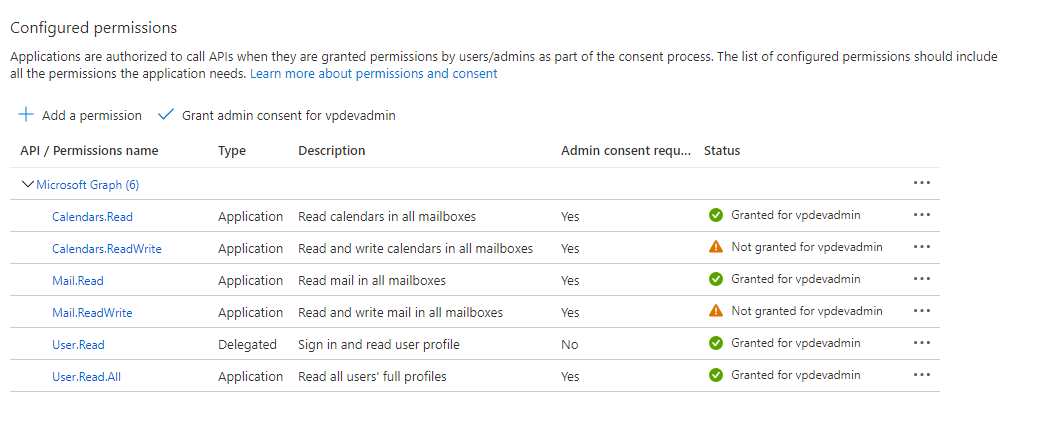
Scenario: If we only want to provide Read permission like Calendar.Read or Mail.Read and want to ensure that ReadWrite permissions for Calendar or Mail (Calendar. ReadWrite or Mail. ReadWrite) is not granted to Riva.
- In Azure, check for the permissions to be removed.
- Use Powershell script to revoke Read.Write permissions – AzureRemovePermissions.ps1
# $ObjectId - object-id of the App Registration e.g. '5f6ac7c6-64c8-4e8a-8e2e-7fb86afdabb4'
# $PermissionsToRemove - List of permisions to be removed e.g. 'Calendars.ReadWrite','Mail.ReadWrite'
# DEBUG
param(
[Parameter(Mandatory=$true)][string] $ApplicationObjectId,
[Parameter(Mandatory=$true)][string[]] $PermissionsToRemove
)
# Add credentials for 1st time, then comment it
#$Credential = Get-Credential # Only for developers
Connect-AzureAD -Credential $Credential
$app = Get-AzureADApplication -ObjectId $ApplicationObjectId
if (!$app)
{
Write-Output "Registered App not found. Please check the ObjectId."
return
}
$resourceAppId = '00000003-0000-0000-c000-000000000000' # Graph API service principal
# Get SP using AppId of registered app
$spApp = Get-AzureADServicePrincipal | Where-Object{$_.AppId -eq $app.AppId}
if (!$spApp)
{
Write-Output "Application not found."
return
}
# Get SP using the ResourceAppId (ResourceAppId is the Application ID of the service principal of the API)
$sp = Get-AzureADServicePrincipal -All $true | Where-Object {$_.AppId -eq $resourceAppId}
if (!$sp)
{
Write-Output "$sp - Permissions not granted or not defined."
return
}
# Fetch the role (permission) for which assignment should be removed
$spRoles = $sp.AppRoles | Where-Object {$_.Value -in $PermissionsToRemove}
if (!$spRoles)
{
Write-Output "$spRoles - Requested Permissions not found."
return
}
#Write-Output $spRoles # DEBUG
# Declare an empty array
$spApplicationPermissions = New-Object System.Collections.ArrayList
# Get application permissions for the service principal, with defined permission, for items defined in removePermissionsList
$spRoles | Foreach-Object {
$currentSpRole = $_
$spApplicationPermission = Get-AzureADServiceAppRoleAssignedTo -ObjectId $spApp.ObjectId -All $true | Where-Object { $_.PrincipalType -eq "ServicePrincipal" } | Where-Object { $_.Id -eq $currentSpRole.Id }
if ($spApplicationPermission)
{
[void]$spApplicationPermissions.Add($spApplicationPermission)
}
}
if ($spApplicationPermissions.Count -eq 0)
{
Write-Output "$spApplicationPermissions - Requested Permissions not found."
return
}
# Remove the intended application permission(s)
$spApplicationPermissions | ForEach-Object {
Remove-AzureADServiceAppRoleAssignment -ObjectId $_.PrincipalId -AppRoleAssignmentId $_.objectId
}
Write-Output "------------------------------------------------------------------------------------------------------------------------------"
Write-Output "Requested permissions removed successfully!"
Find 2 mandatory parameters:
- Provide registered application’s Object Id - param name -ApplicationObjectId
How to find a registered application’s object ID
- Go to portal.azure.com
- Click on Azure Active Directory
- Click on Enterprise Applications and search for the app
- Click on the App
- Copy Object ID
.png)
- Provide a list of permissions to be revoked – param name -PermissionsToRemove
The example shown below with 'Mail.ReadWrite','Calendars.ReadWrite'
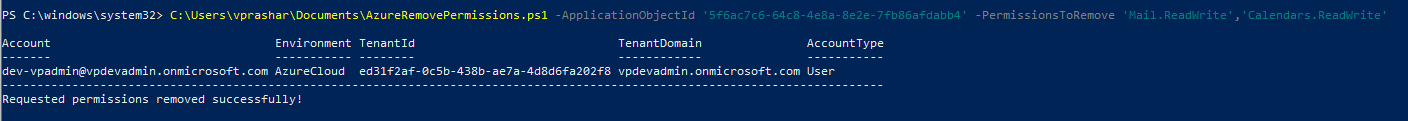
C:\Users\vprashar\Documents\AzurePermissions.ps1 -ApplicationObjectId '5f6ac7c6-64c8-4e8a-8e2e-7fb86afdabb4' -PermissionsToRemove 'Mail.ReadWrite','Calendars.ReadWrite
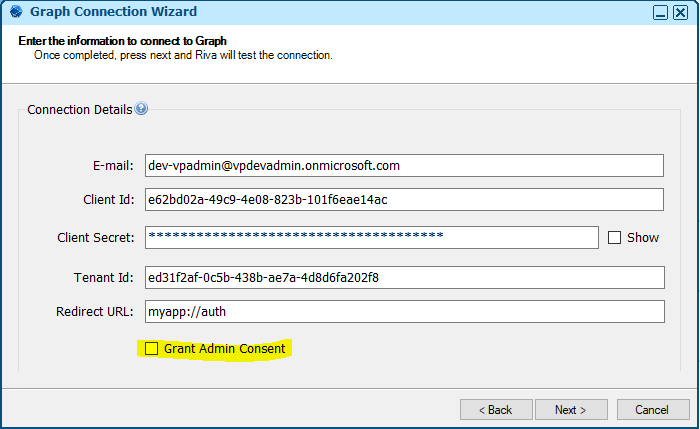
- Create a Graph connection using Riva - no admin consent – Checkbox is unchecked
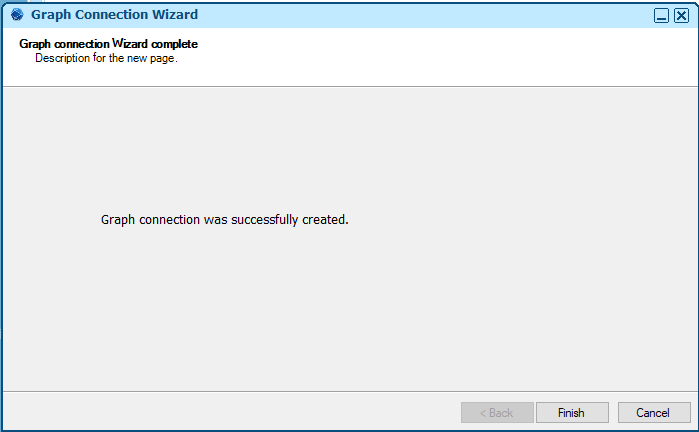
- No consent screen appears and the connection is created successfully.
Verification Steps: Depending upon which permissions are added or revoked, a test can be run by running a sync. Use the Graph connection created and sync.
- Example scenario
- Calendar.ReadWrite revoked and Calendar.Read added
- Result: Perform a Create or Update through sync – Create or update should fail.








.png)




