|
Article ID: 2112
Last updated: 03 Mar, 2021
Applies to Riva On-Premise.
Purpose of This Article
Connecting Office 365 in RivaIt is possible to set up an Office 365 connection in Riva using one of the following options:
For more information, see
OAuth Authorization Code Grant FlowThis flow typically requires a Client Secret along with Tenant Id, Application Id, and Reply URL. Currently, Riva requests Access Tokens as a web app, which makes client_secret a required field, as stated by Microsoft. To change this behaviour, create Mobile and desktop applications redirect URIs in Azure, under the application’s Platform configurations. These redirect URIs do not require a client_secret. For more information, see Microsoft identity platform and OAuth 2.0 authorization code flow.
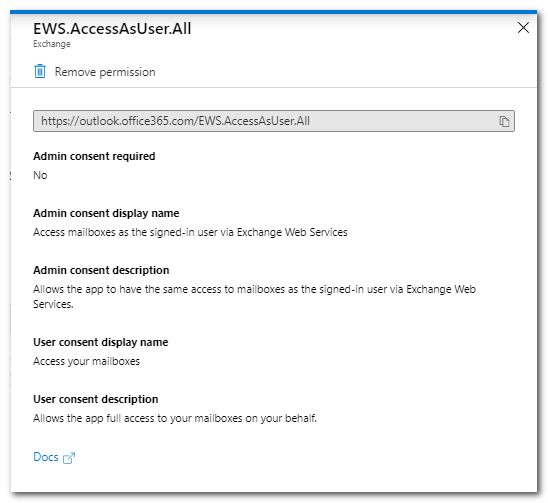
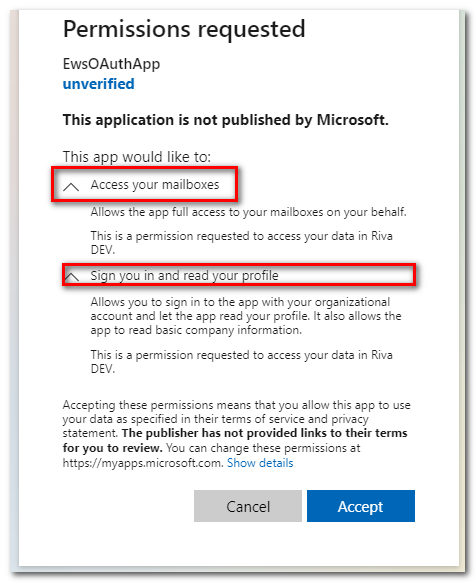
OAuth Permission to Access EWS APIs in Exchange Online To use OAuth Authorization Code Grant Flow with Riva, it is recommended to configure the Azure Active Directory App to have Delegated permissions in order to access EWS APIs in Exchange Online. Apps with a signed-in user can have delegated permissions. Administrators or users can consent to the app's request for permissions. The app can then make API calls while acting as the signed-in user. For more information, see Authenticate an EWS application by using OAuth. The app will then have the same access to mailboxes as the signed-in user via Exchange Web Services (EWS). Any Application Impersonation roles configured in Exchange for restricting mailbox access will be respected.
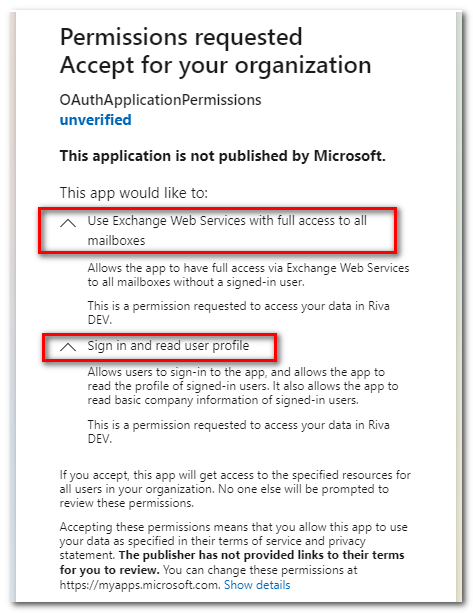
Here is an Azure consent page for Riva, configured with delegated permissions. Note the specific permissions requested:
Restricting Which Mailboxes an Azure Application Can AccessIf the Azure application accessed by Riva is configured to use delegated permissions, it will access EWS as the signed-in user. With that in mind, it is possible to configure the service account that signs in the Azure application to impersonate a selected number of mailboxes only. This function can be accomplished through the Exchange Management Shell. How Does Impersonation Restriction work with OAuth and Riva?Here is an example of impersonation restriction that uses OAuth Authorization Code Grant Flow, Exchange management scopes, and Riva. For complete instructions, refer to Microsoft documentation. This example discusses the following resources:
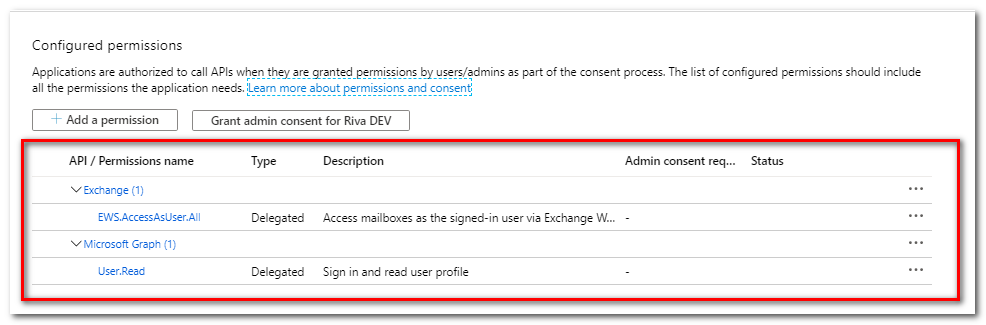
For more information, see Prepare Office 365 Exchange permissions for Riva connections. The first step is to create the Azure app registration. The app will then have the following configuration:
The second step is to configure the service account by following the Microsoft documentation. The account was configured with the following rules:
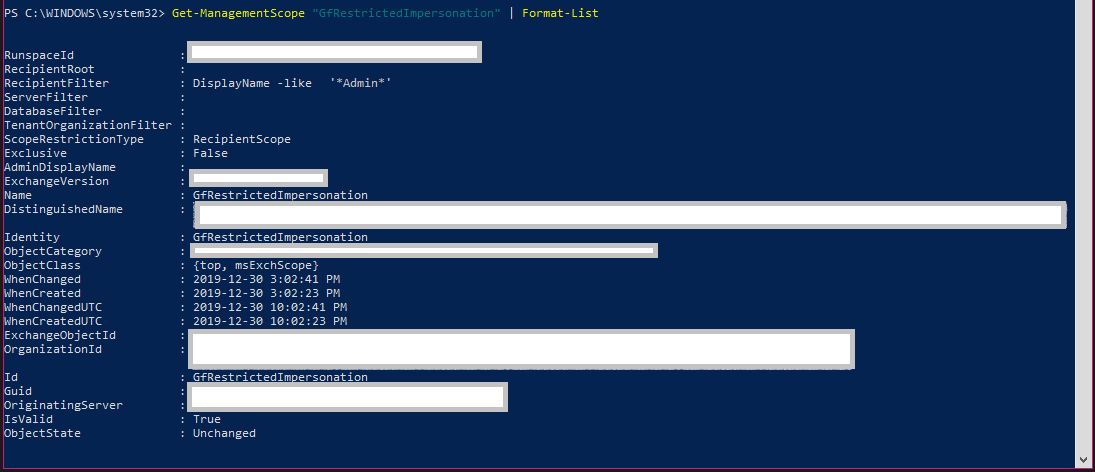
Management Scope created in Exchange:
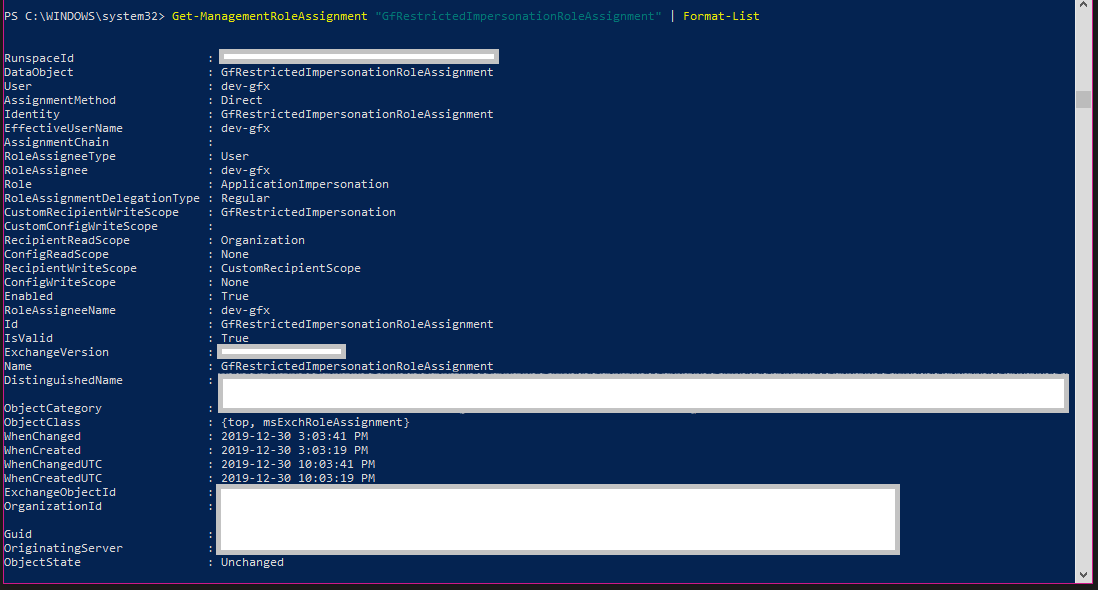
Management Role Assignment created in Exchange:
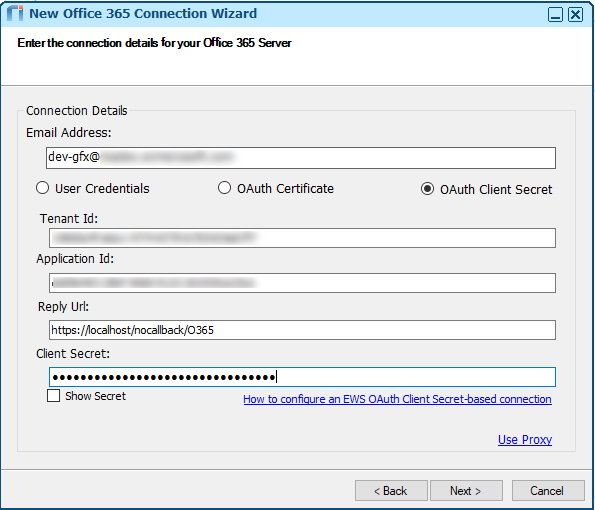
This is an Office 365 connection in Riva On-Premise that uses the OAuth Client Secret authorization method:
The Azure consent page requests permissions:
Riva connection test: Successfully impersonated the mailbox dev-gf1:
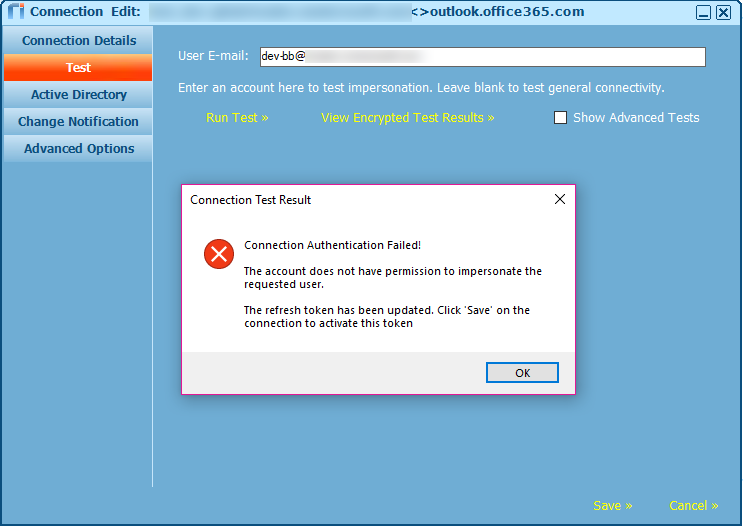
Riva connection test: Failed to impersonate the mailbox dev-bb. The service account is not allowed to impersonate this user.
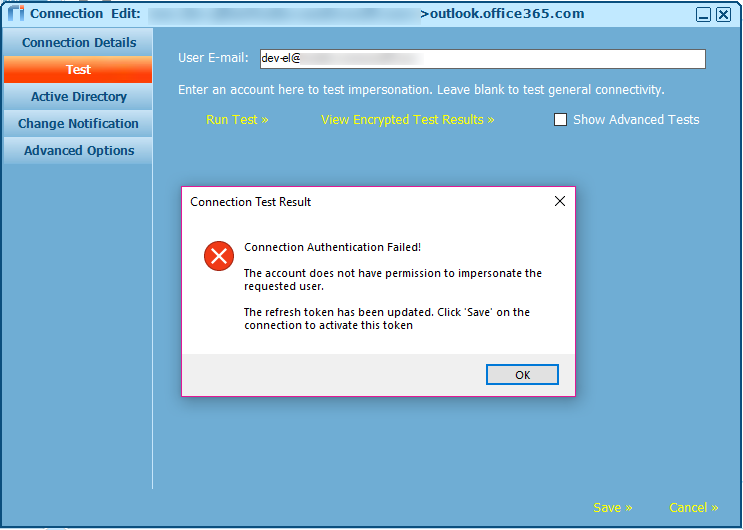
Riva connection test: Failed to impersonate the mailbox dev-el. The service account is not allowed to impersonate this user.
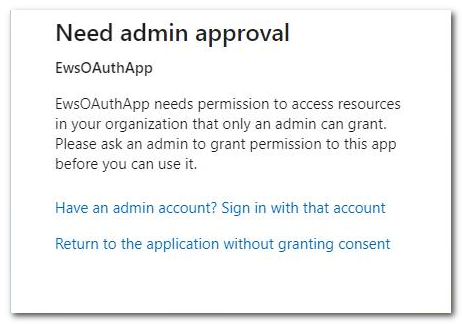
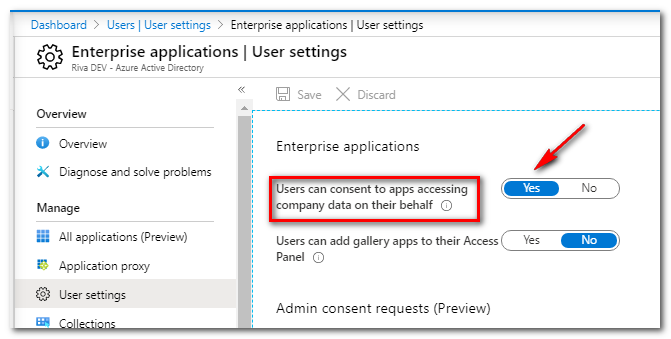
Note: If the service account is a non-admin user and a message related to “admin approval” is displayed (as shown below), you can enable the option “Users can consent to apps accessing company data on their behalf” in Azure Active Directory Admin Center. For more information, see Configure how end-users consent to applications.
There are further options for the approval process workflow, and it is also possible to limit the approval for apps based on user groups. For more information, see Microsoft's documentation:
To continue the workflow, enable user consent in Azure as shown, if permitted by your organization:
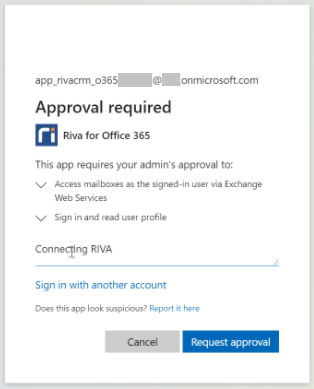
If administrator approval is mandatory in your organization, you will need to request approval in the dialog box (as shown below). Once the request is approved by your Office 365 administrator, you can complete the OAuth setup as above.
OAuth Client Credentials Flow (Supports Certificates)OAuth Client Credentials Flow allows a confidential client to use its own credentials to authenticate with another web service. This removes the need to impersonate a user during authentication. The web service can then use a certificate as a credential. This flow requires “Application Permissions”, which means that after the app authenticates, it gets full access to all of the organization's mailboxes. The scoping features available for Microsoft Graph do not work with the EWS API.
For more information, see Microsoft identity platform and the OAuth 2.0 client credentials flow. Basic AuthenticationBasic Authentication requires the application to pass a user name and password in order to authenticate and have access to resources. Although simple, it is less secure than Modern Authentication methods like OAuth. Microsoft announced the end of support for Basic Authentication for Exchange Web Services (EWS) to access Exchange Online. Existing customers who use Basic Authentication will have grace period access until mid-2021. For more information, see End of support for Basic Authentication access to Exchange Online APIs for Office 365 customers and Upcoming changes to Exchange Web Services (EWS) API for Office 365. Note: These changes to Basic Authentication apply only to the cloud-based Office 365/Exchange Online products; there are no changes to EWS capabilities of on-premises Exchange products.
This article was:
Helpful |
Not helpful
Report an issue
Article ID: 2112
Last updated: 03 Mar, 2021
Revision: 38
Views: 0
Comments: 0
|
.png)
.png)