|
Article ID: 912
Last updated: 14 Aug, 2015
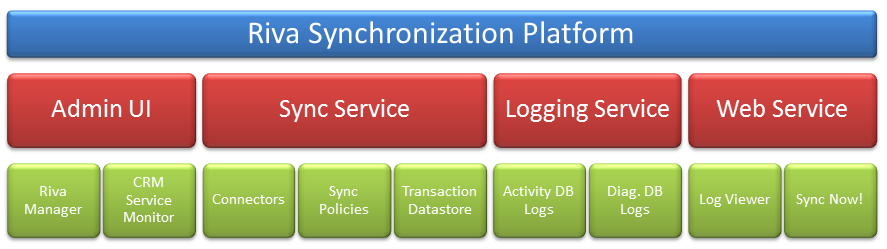
The following diagram shows a high-level overview of the Riva synchronization solution components.
|
| Admin UI | Service Monitor |
|---|---|
 |
 |
Riva Cloud
| Admin UI | Service Monitor |
|---|---|
.png) |
 |
Riva Sync Service
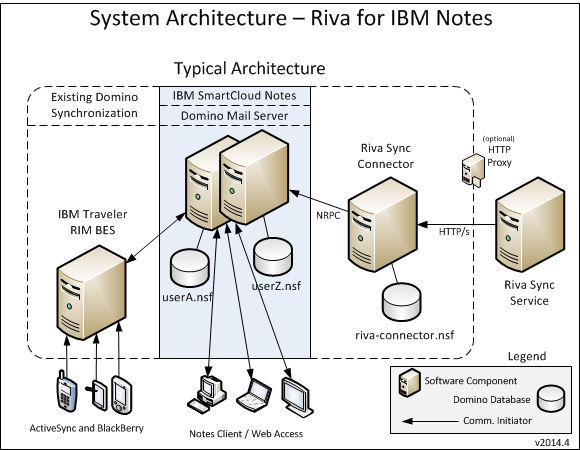
Synchronisation services are provided by the Riva Sync Service. It synchronises data between the Riva Sync Connector and and the target CRM. The following diagram shows the individual components of the synchronization services. Not all components are required and not all are included in a default configuration. The diagram also includes data flow and access patterns.
.png)
Security Access Levels
The synchronization service should be configured with network credentials with elevated privileges. This is the recommended configuration for each connector configured with Riva because Riva synchronizes data on behalf of other users.
If elevated privileges are not available, individual connections must be created for each user. This "personal connection" configuration is not practical in an large deployment where on-going password changes make for a management burden.
IBM Notes / IBM Domino Connector: Details on the configuration requirements of the connection user can be found here.
CRM Connector: Each CRM has specific connection requirements. These can be found in the deployment and configuration guides for the connector. Each CRM will support a different impersonation model. Details can be found here.
Encryption
Data is encrypted at multiple different points,
- Network Communication
- Credentials Security
Network Communication: All communication to the Riva Sync Connector can be encrypted using SSL over HTTP. Because the connector is configured in Domino, all native IBM web security practices apply. Once the Domino server is configured with SSL, ensure the connection details configured include "https" as the scheme.
The communication and network traffic between the Riva synchronization service and each configured target system is dependent on the URL scheme provided during the connection wizard process. If the URL begins with https://, Riva will establish a secure tunnel using the provided SSL certificate to the destined HTTP service.
It is always recommends the use of HTTPS whenever possible and available.
Credentials Security: The internal configuration files used to maintain the connection details including credentials are stored in a set of encrypted files. The connection manager leverages the AES-256. These files are stored on the Riva synchronization services files system and are never left in an unencrypted state.
Data Storage
As a core principal, during synchronization, none of the Riva components cache or write the message content of emails or store any private information for opportunities, cases, quotes, projects, contacts, accounts, appointments, etc. to any persistent storage on the Riva servers at any time. This information is retrieved, received, converted, transformed, transmitted and an absolute minimal information sub-set is stored.
In order to synchronize, Riva persists certain minimum types of information for core functionality and performance improvement. Some of this information includes data fields like the unique record database ID, modification date time stamps and item change revisions. This information is kept in persistent storage unique to each user. This persistent storage is referred to as the transaction database or as metadata.
If the metadata is opened using query tools, it is not possible to re-create the item or to determine any details about the content that had previously synchronized from the information stored in the metadata. The metadata alone cannot be used to build or restore any information that has been previously synchronized.
Riva considers content fields to be fields like: email or appointment subject, location, body, attachments, attendee or recipients lists. These fields and those like it which contain “content relevant to the record intention” is never stored in the metadata.
For performance reasons, by default, Riva stores a dynamic mapping of email addresses and website domains for related contacts and accounts that have been synchronized. This avoids the additional network communication required for common relationship look-ups when the information is available for items that have already processed. This greatly improves scalability and reduces synchronization times when handling relational data in reference to email recipients and appointment attendees. Additional configuration can adjust this behavior so that the raw values are not stored resulting instead in a hash of the email addresses or optionally this optimization can be completely disable to ensure data privacy.
No information that is being synchronized is stored in the Riva Sync Connector, this component acts purely as a data transformation gateway service.
Additional temporary storage of information is logged and logging is described further in detail below.
High Availability / Fault Tolerance
The Riva Sync Connector for IBM Notes software that is installed as a Domino database supports replication allowing for high-availability if a server becomes unavailable.
More details on IBM Domino high-availability can be found here.
Logging Services
Logging is an essential part of any data integration solution. Logging provides evidence to the current state of the synchronization at a specific moments in time allowing in-depth analysis of synchronization conditions. Due to the complexities of today's networks, the number of different Notes enabled devices and clients, the logging services provide details as to when, and why a specific record was created, modified or deleted.
By default logs are stored on the local file system with an option to move the logs to a relational database.
The following resources provide insight into the logging services,